Services
TALK TO AN EXPERTOur Services
Explore our comprehensive range of services that form the bedrock of our partnership with your business!.
Our specialised expertise and advance methodologies are in place to ensure your application, network infrastructure, and cloud environments are both robust and impenetrable.
With subscription services catered to your needs, you’ll be able to gain continuous monitoring and real-time threat intelligence, strengthening your defence against evolving cyber threats.
Red Team Partners offers the following services:
- Application Testing
- Infrastructure Testing
- Social Engineering
- Accreditations
- Subscription Services (One-time Analysis / Monthly / Quarterly)
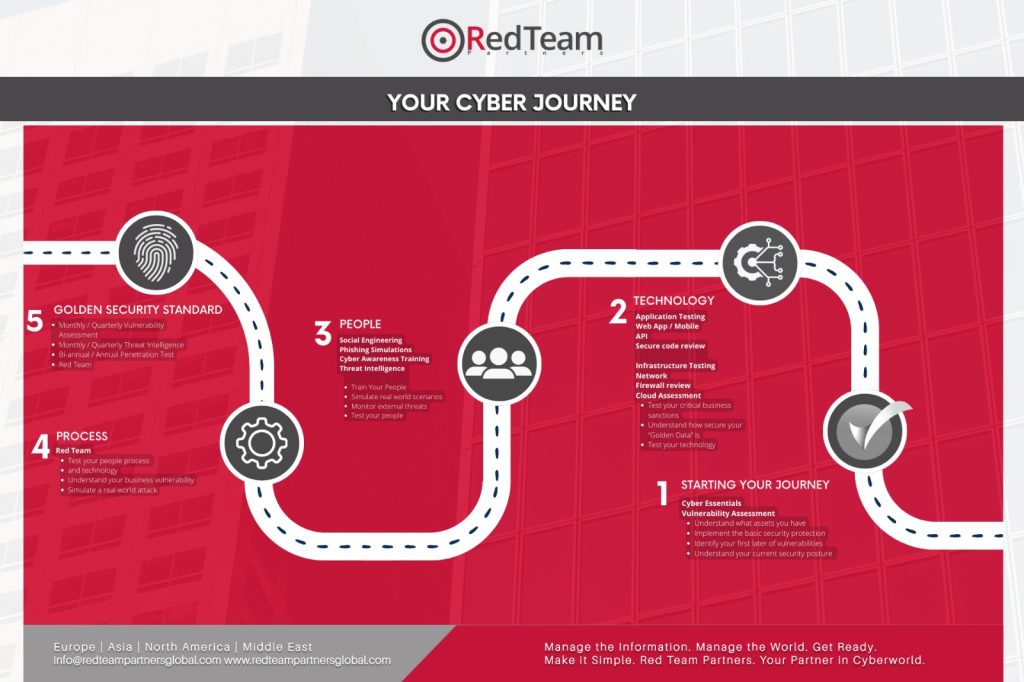
Your Cyber Journey
Staying secure should be easy, beside is the roadmap that can help you on your cyber journey. Covering people, processes and technology this roadmap can help you understand where you are at the moment and your next step on your cyber journey. Red Team Partners is here to help your business stay secure against cyber attacks, we know that the cyber journey isn’t easy for a business. We are helping hundreds of companies stay secure by identifying cyber issues and providing relief that their company is secure. Book a call with us to discuss further.
-
Application Testing
Application Testing
Mobile Application
Web Application
Secure Code View -
Infrastructure Testing
Infrastructure Penetration Testing
Firewall Review
Cloud Assessment/Review -
Social Engineering
Phishing Simulation
Red Team Assessment
Cyber Awareness Training -
Accreditations
Cyber Essentials Basic
Cyber Essentials Plus
ISO 27001 Consultancy -
Subscription Services
Application Vulnerability Assessment
Infrastructure Vulnerability Assessment
Cyber Threat Intelligence
Application Testing
API Penetration Testing
Test to ensure that the APIs are functioning correctly, are reliable, and perform well. API testing can also help to improve security.
MobileApplication Testing (iOS/Android)
Mobile application testing is just one of the many processes involved to make sure an app is successful from end-to-end.It helps you avoid releasing a substandard product to the market.
Web Application Penetration Testing
Web testing is a process of verifying the functionality of a web application. This can be done prior to a release, or on a day-today basis to ensure quality. Web testing allows you to find bugs in the software, which can then be fixed prior to a release.
Secure Code Review
This code review is a systematic examination (sometimes referred to as peer review) of computer source code. It is intended to find mistakes overlooked in software development, improving the overall quality of software.
Infrastructure Testing
Infrastructure Penetration Testing
This is an effective process of identifying vulnerabilities and weaknesses within your organization’s network infrastructure. It prevents malicious access or loss of confidential data due to IP/ server attacks or internal attacks (servers, workstations, network devices).
Firewall Review
A poorly configured firewall can allow for trivial network compromise by malicious actors. Red Team Partners firewall assessment will test the integrity of your current firewall rules and implementations to ensure nothing has been overlooked.
Cloud Assessment/Review
(AWS/Azure/O365) Deep dive into your cloud environment and provides an assessment of where your company stands and what you need to do to improve security.
Social Engineering
Phishing Simulation
Phishing is one of the most common paths to compromise utilised by attackers in realworld attacks. Phishing Simulation aims to highlight weak security controls and susceptible employees to target for further in-depth phishing awarenesstraining.
Red Team Assessment
A thorough investigation of the organisation’s security in order to identify and weaknesses that could be exploited by a skilled illegal cyber hackers.
Cyber Awareness Training
Cyber Awareness Training for your workforce. Our training can be customized to your needs. It will educate your employees about cyber threats, policies, and legal compliance, and standard operating procedures in addressing the issue to help produce better service and attract customers.
Accreditations
Cyber Essentials Basic (UK Accreditation)
Cyber Essentials Basic provides a range of benefits and is something anyone can use to protect themselves from cyber threats. Whether you have a small business or work for an enterprise, it’s easy to get Cyber Essentials certification through Red Team Partners. This will help you to protect your business against a whole range of the most common cyberattacks.
Cyber Essentials Plus (UK Accreditation)
Cyber Essential Plus is a step up from the standard. With it, you’ll get the same simplicity of approach and the same traditional controls to put in place, but this version adds a hands-on technical verification on top of everything else. Meeting compliance standards can be a tedious and time- consuming process but with our team of experts, we can help you get your certification in less than 24 hours. We make it easy by guiding you through a short questionnaire, matching your needs with the appropriate security requirements, and providing remote CE+ audits.
ISO 27001 Consultancy (Global Accreditation)
Providing requirements for an information security management system (ISMS), though there are more than a dozen standards in the ISO/IEC 27000 family. Using them enables organisations of any kind to manage the security of assets such as financial information, intellectual property, employee details or information entrusted by thirdparties.
Subscription Services (One-time Analysis / Monthly / Quarterly)
Application Vulnerability Assessment (Black Box / Without Credentials)
A vulnerability assessment is a systematic review of your company’s Internet-facing systems, checking for potential security weaknesses. It is important that you’re aware of these issues – misconfigurations and outdated software could put your systems and data at risk. This assessment will help you find, prioritize, and fix these weaknesses before they can be exploited.
Infrastructure Vulnerability Assessment
A vulnerability assessment is a systematic review of your company’s Internet-facing systems, checking for potential security weaknesses. It is important that you’re aware of these issues – misconfigurations and outdated software could put your systems and data at risk. This assessment will help you find, prioritize, and fix these weaknesses before they can be exploited.
Cyber Threat Intelligence
Security is one of your top priorities and the dark web is the new frontier. Our Cyber Threat Intelligence service provides actionable intelligence to help you navigate this new landscape. We have developed an assessment that identifies dark web-based emerging threats and vulnerabilities to protect your company’s most valuable assets and confidential data.
